We all are very familiar with Apache web server, it is a very popular web server to host your web files or your website on the web. Here are some links which can help you to configure Apache web server on your Linux box.

Install Apache Web Server
Setup Your Website in Your Linux Box
Here in this tutorial, I’ll cover some main tips to secure your web server. Before you apply these changes in your web server, you should have some basics of the Apache server.
- Document root Directory: /var/www/html or /var/www
- Main Configuration file: /etc/httpd/conf/httpd.conf (RHEL/CentOS/Fedora) and /etc/apache2/apache2.conf (Debian/Ubuntu).
- Default HTTP Port: 80 TCP
- Default HTTPS Port: 443 TCP
- Test your Configuration file settings and syntax: httpd -t
- Access Log files of Web Server: /var/log/httpd/access_log
- Error Log files of Web Server: /var/log/httpd/error_log
1. How to hide Apache Version and OS Identity from Errors
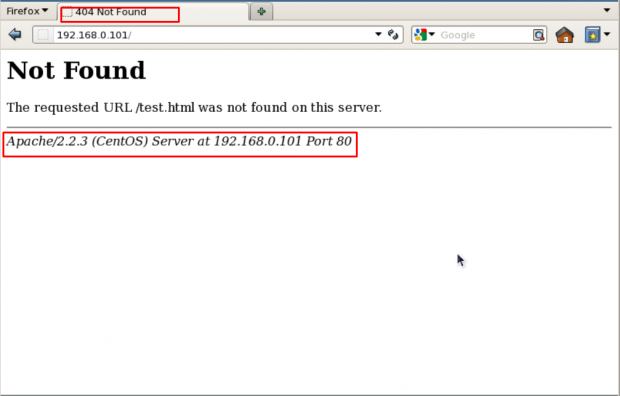
When you install Apache with source or any other package installers like yum, it displays the version of your Apache web server installed on your server with the Operating system name of your server in Errors. It also shows the information about Apache modules installed in your server.
In above picture, you can see that Apache is showing its version with the OS installed in your server. This can be a major security threat to your web server as well as your Linux box too. To prevent Apache to not to display these information to the world, we need to make some changes in Apache main configuration file.
Open configuration file with vim editor and search for “ServerSignature“, its by default On. We need to Off these server signature and the second line “ServerTokens Prod” tells Apache to return only Apache as product in the server response header on the every page request, It suppress the OS, major and minor version info.
# vim /etc/httpd/conf/httpd.conf (RHEL/CentOS/Fedora) # vim /etc/apache2/apache2.conf (Debian/Ubuntu)
ServerSignature Off ServerTokens Prod
# service httpd restart (RHEL/CentOS/Fedora) # service apache2 restart (Debian/Ubuntu)

2. Disable Directory Listing
By default Apache list all the content of Document root directory in the absence of index file. Please see the image below.

We can turn off directory listing by using Options directive in configuration file for a specific directory. For that we need to make an entry in httpd.conf or apache2.conf file.
<Directory /var/www/html>
Options -Indexes
</Directory>

3. Keep updating Apache Regularly
Apache developer community is continuously working on security issues and releasing its updated version with new security options. So It is always recommended to use the latest version of Apache as your web server.
To check Apache version: You can check your current version with httpd -v command.
# httpd -v Server version: Apache/2.2.15 (Unix) Server built: Aug 13 2013 17:29:28
You can update your version with the following command.
# yum update httpd # apt-get install apache2
It is also recommended to keep your Kernel and OS updated to the latest stable releases if you are not running any specific application which works only on specific OS or Kernel.
4. Disable Unnecessary Modules
It’s always good to minor the chances of being a victim of any web attack. So it’s recommended to disable all those modules that are not in use currently. You can list all the compiled modules of web server, using following command.
# grep LoadModule /etc/httpd/conf/httpd.conf # have to place corresponding `LoadModule' lines at this location so the # LoadModule foo_module modules/mod_foo.so LoadModule auth_basic_module modules/mod_auth_basic.so LoadModule auth_digest_module modules/mod_auth_digest.so LoadModule authn_file_module modules/mod_authn_file.so LoadModule authn_alias_module modules/mod_authn_alias.so LoadModule authn_anon_module modules/mod_authn_anon.so LoadModule authn_dbm_module modules/mod_authn_dbm.so LoadModule authn_default_module modules/mod_authn_default.so LoadModule authz_host_module modules/mod_authz_host.so LoadModule authz_user_module modules/mod_authz_user.so LoadModule authz_owner_module modules/mod_authz_owner.so LoadModule authz_groupfile_module modules/mod_authz_groupfile.so LoadModule authz_dbm_module modules/mod_authz_dbm.so LoadModule authz_default_module modules/mod_authz_default.so LoadModule ldap_module modules/mod_ldap.so LoadModule authnz_ldap_module modules/mod_authnz_ldap.so LoadModule include_module modules/mod_include.so LoadModule log_config_module modules/mod_log_config.so LoadModule logio_module modules/mod_logio.so LoadModule env_module modules/mod_env.so LoadModule ext_filter_module modules/mod_ext_filter.so ....
Above is the list of modules that are enabled by default but often not needed: mod_imap, mod_include, mod_info, mod_userdir, mod_autoindex. To disable the particular module, you can insert a “#” at the beginning of that line and restart the service.
5. Run Apache as separate User and Group
With a default installation Apache runs its process with user nobody or daemon. For security reasons it is recommended to run Apache in its own non-privileged account. For example: http-web.
Create Apache User and Group
# groupadd http-web # useradd -d /var/www/ -g http-web -s /bin/nologin http-web
Now you need to tell Apache to run with this new user and to do so, we need to make an entry in /etc/httpd/conf/httpd.conf and restart the service.
Open /etc/httpd/conf/httpd.conf with vim editor and search for keyword “User” and “Group” and there you will need to specify the username and groupname to use.
User http-web Group http-web
6. Use Allow and Deny to Restrict access to Directories
We can restrict access to directories with “Allow” and “Deny” options in httpd.conf file. Here in this example, we’ll be securing root directory, for that by setting the following in the httpd.conf file.
<Directory /> Options None Order deny,allow Deny from all </Directory>
- Options “None” – This option will not allow users to enable any optional features.
- Order deny, allow – This is the order in which the “Deny” and “Allow” directives will be processed. Here it will “deny” first and “allow” next.
- Deny from all – This will deny request from everybody to the root directory, nobody will be able to access root directory.
7. Use mod_security and mod_evasive Modules to Secure Apache
These two modules “mod_security” and “mod_evasive” are very popular modules of Apache in terms of security.
Mod_security
Where mod_security works as a firewall for our web applications and allows us to monitor traffic on a real time basis. It also helps us to protect our websites or web server from brute force attacks. You can simply install mod_security on your server with the help of your default package installers.
Install mod_security on Ubuntu/Debian
$ sudo apt-get install libapache2-modsecurity $ sudo a2enmod mod-security $ sudo /etc/init.d/apache2 force-reload
Install mod_security on RHEL/CentOS/Fedora/
# yum install mod_security # /etc/init.d/httpd restart
8. Securing Apache with SSL Certificates
Last, but not the least SSL certificates, you can secure your all the communication in an encrypted manner over the Internet with SSL certificate. Suppose you have a website in which people login by proving their Login credentials or you have an E- Commerce website where people provides their bank details or Debit/Credit card details to purchase products, by default your web server send these details in plain – text format but when you use SSL certificates to your websites, Apache sends all this information in encrypted text.
You can purchase SSl certificates from So many different SSL providers like namecheap.com. If you are running a very small web business and do not willing to purchase an SSL certificate you can still assign a Self signed certificate to your website. Apache uses the mod_ssl module to support SSL certificate.
# openssl genrsa -des3 -out example.com.key 1024 # openssl req -new -key example.com.key -out exmaple.csr # openssl x509 -req -days 365 -in example.com.com.csr -signkey example.com.com.key -out example.com.com.crt
Once your certificate has been created and signed. Now you need to add this in Apache configuration. Open main configuration file with vim editor and add the following lines and restart the service.
<VirtualHost 172.16.25.125:443>
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/example.com.crt
SSLCertificateKeyFile /etc/pki/tls/certs/example.com.key
SSLCertificateChainFile /etc/pki/tls/certs/sf_bundle.crt
ServerAdmin ravi.saive@example.com
ServerName example.com
DocumentRoot /var/www/html/example/
ErrorLog /var/log/httpd/example.com-error_log
CustomLog /var/log/httpd/example.com-access_log common
</VirtualHost>
Open up your browser, type https://example.com, and you will be able to see the new self-signed certificate.
These are few security tips that you can use to secure your Apache web server installation. For more useful security tips and ideas, see the official online documentation of Apache HTTP Server